Lab 5: Communications Forensics
When you're done with this lab you will have done the following things:
- Extracted and explained significance of E-Mail Metadata
- Analyzed network traffic to identify types and sources/destinations
- Captured network traffic using Wireshark
- Extracted content from observed network traffic to identify what happened
Throughout this entire lab (and this course), this web site assumes you are using the RHIT-supplied image of Windows and that you're working in partners out of the Digital Forensics Workbook (Michael K. Robinson).
Expectations
Keep in mind as you work on this lab that your efforts must be Repeatable and Reproducible.
Document your steps as you do them. At the end of each part (chapter), be sure to update your lab notebook with a short summary or conclusion, then write your names (or sign) and date it.
When you acquire evidence or artifacts, you must document:
- What the evidence item is (e.g., usb drive or a file)
- Where the evidence came from
- How the evidence was acquired
Chapter 12: E-Mail Analysis
Read chapter 12 and follow the instructions it contains.
Do activity 12-1
You can obtain the e-mail_headers.zip file from the
mirror.
Do the additional exercises in 12-1
Chapter 22: Network Traffic
Read chapter 22 and follow the instructions it contains.
Wireshark is available from the wireshark website.
You can obtain all of the .pcapng data files from the
mirror.
Do activity 22-1
SKIP the additional exercises in 22-1
Do activity 22-2
SKIP activity 22-3
Do activity 22-4
Step 6: The menu has changed. You will have to select the "Follow..." submenu after you right-click, and choose "TCP Stream" from that submenu.
Step 11: The timestamp in the text is wrong (the screenshot is correct). The last modified date should be "Sun, 06 Sep 2015 12:19:52 GMT".
Do activity 22-5
Secure Web Sites: AKC is now a secure (HTTPS) site, which means it is difficult to glean information from the server using wireshark. If you have trouble following the steps, use the site http://web.mit.edu instead and describe why you're doing this in your lab report.
NOTE: Wireshark's main UI screen has changed. It will look a little different.
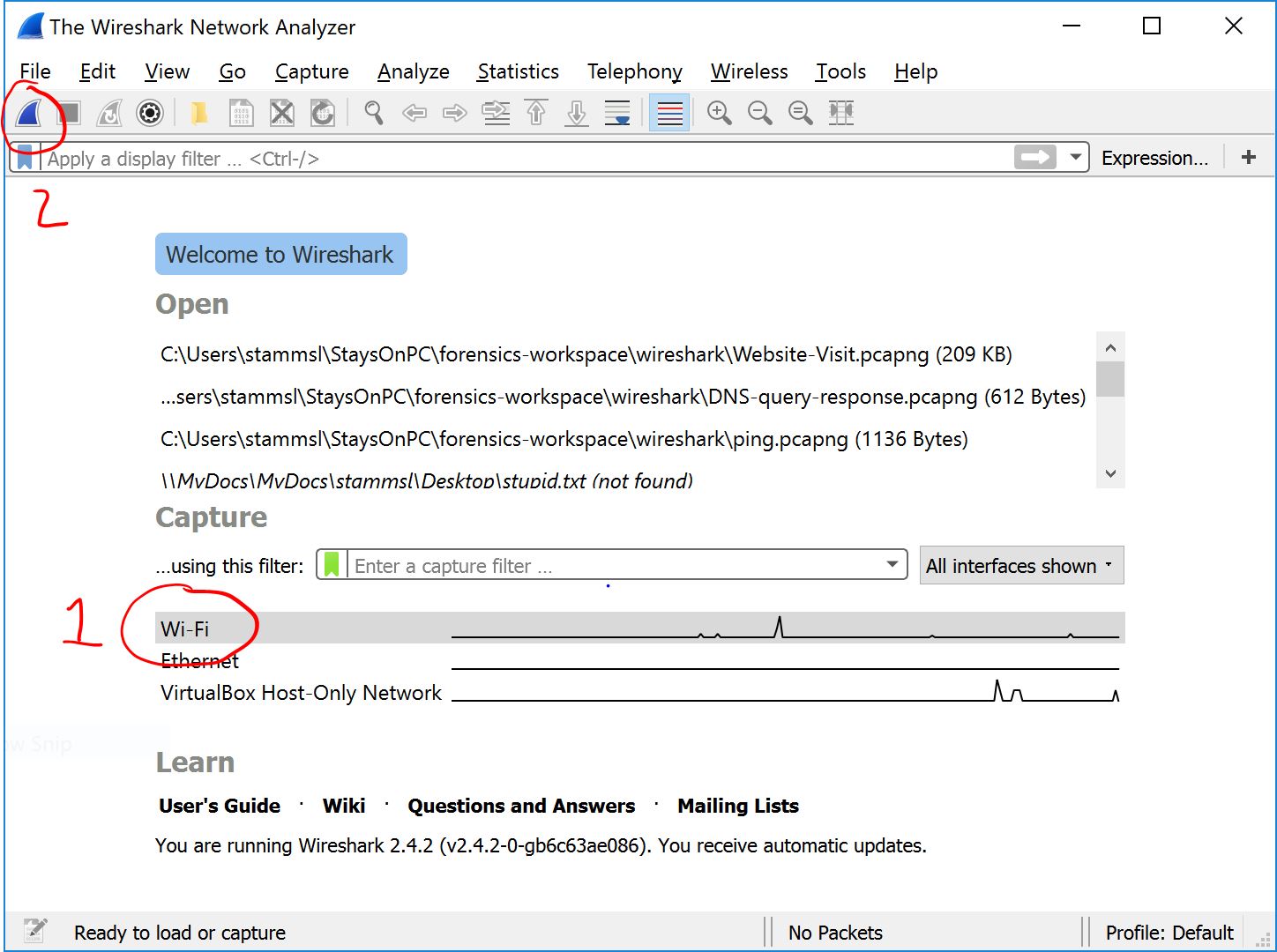
Step 2: If you are using WiFi to access the internet, you will need to select your wireless interface for capture. Instead of capturing on Local Area Connection as the book says, choose the WiFi interface (1 below), then click the blue shark fin in the toolbar (2 below).
Figure 22-14 (step 5) should look like this:
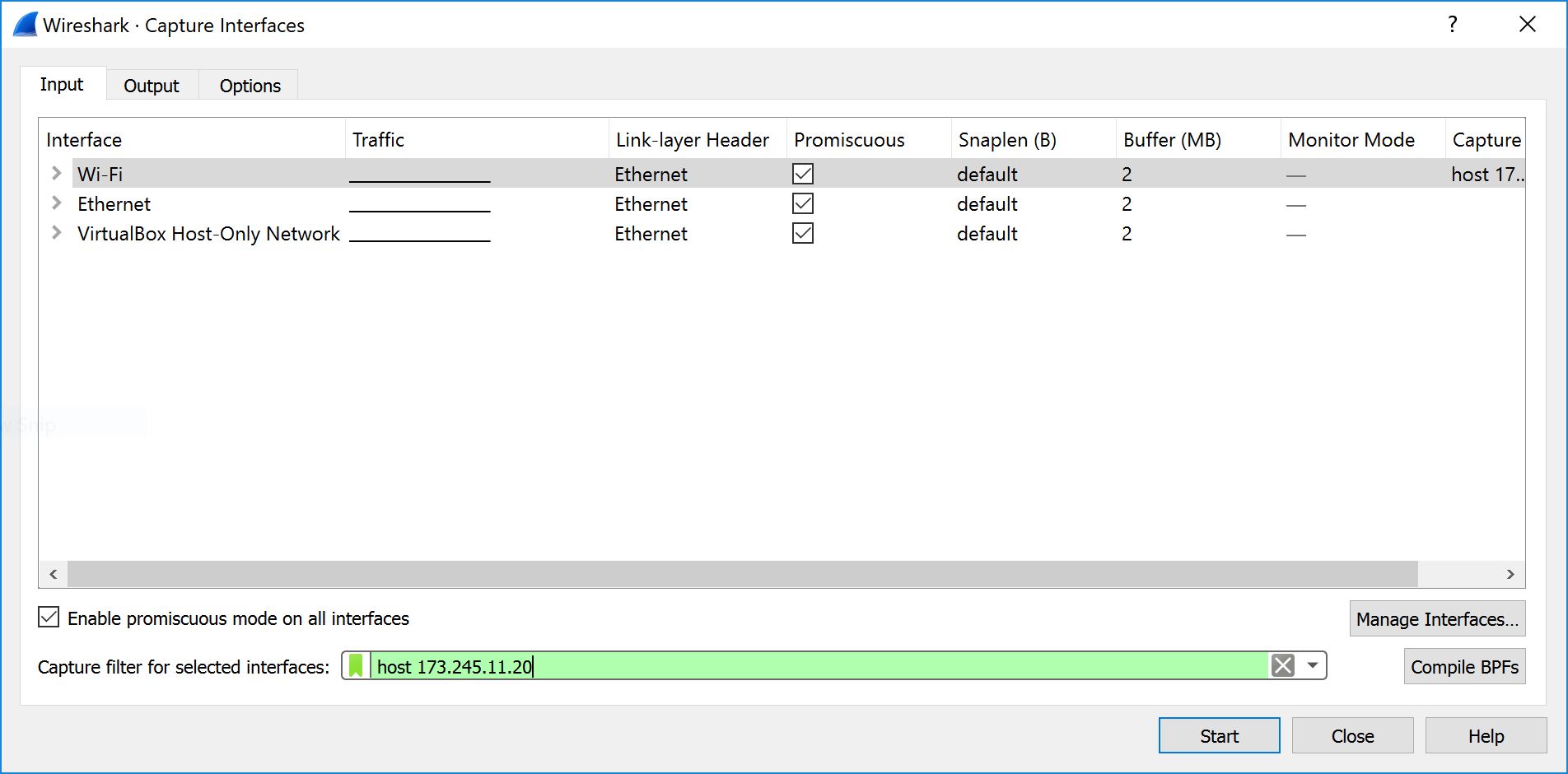
Step 7: The IP address for the host filter is wrong. Instead, use 23.185.0.4. (NOTE: if you used web.mit.edu, this host filter won't work. You will need to skip this step and do a little hunting in the capture screen to find the right packets.)
Step 13: The web server may be "nginx", not Apache.
Step 17: Your results may vary (particularly the date). Record what you find.
Skip Additional Exercises at the end of 22-5
Finishing This Lab
When you're done with this lab, read over your lab notebook and ensure you've properly documented what you've done and with what you've worked.
Submit your lab write-up for grading (to moodle in PDF format) when you are done with the lab.